Unethical hacking is the other side of the coin to the more popular ethical hacking. Hackers used illegal hacking techniques to rake in rapid cash. There are, however, many people who prefer to learn hacking the right way. Ethical hacking extends to areas such as WiFi protocol study and WiFi security. Therefore, you need to learn how to properly use specific instruments if you want to become an expert ethical hacker. With these resources, the security industry could eliminate a lot of unnecessary complexity. We’ve compiled a list of the Best Windows, Linux, and mac hacking tools, replete with in-depth descriptions of their capabilities.
20 Best Windows, Linux, and mac hacking tools
So, in this article, we will share the best Windows, Linux, and mac hacking tools. The majority of the recommended resources were available at no cost. Please use the information here only for its intended purpose of education.
Metasploit
Instead of calling it an exploit toolkit, I’ll refer to Metasploit as a foundation for building new tools. One of the most popular free cybersecurity tools, this application can scan for vulnerabilities in many different systems.
Over 200 thousand Metasploit users and volunteers are here to help you find loopholes in your security and gain insights.
Nmap
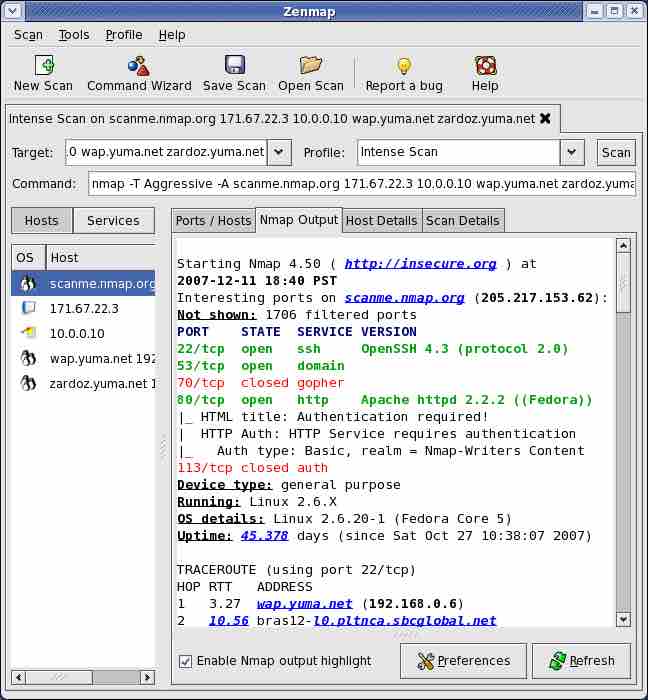
Nmap works with Windows, Linux, and Mac OS X. Free and open-source tool Nmap (Network Mapper) may be used to conduct both network discovery and vulnerability assessments. I think most people are familiar with it.
In addition to being optimized for scanning large networks, it performs well when scanning single hosts. You can use it to create a “map” of a computer network by identifying the computers and services that make up the network.
Acunetix WVS
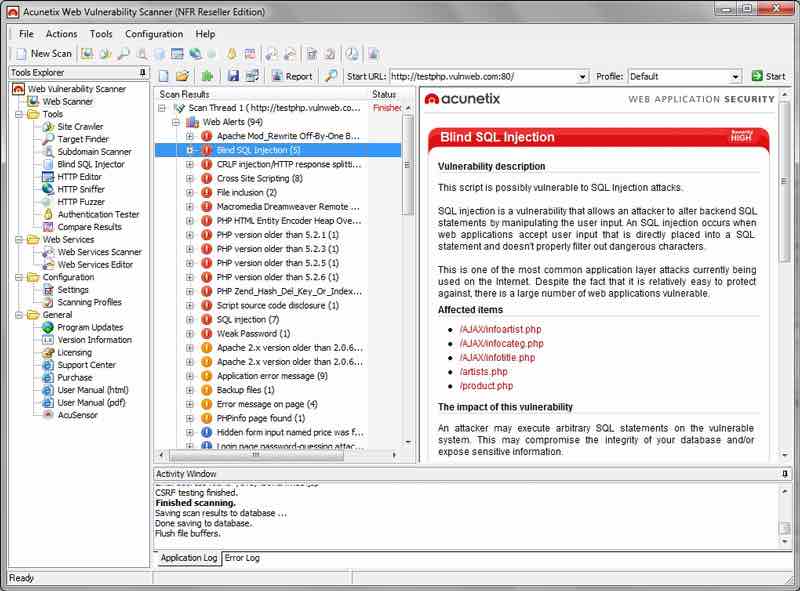
It works fine with Windows XP SP3 and later versions. It is also known as one of the best mac hacking tools. Acunetix is a WVS (web vulnerability scanner) that analyzes websites for security flaws.
This application uses multiple threads to probe a website for security flaws like Cross-site Scripting and SQL injection. This simple and fast scanner checks WordPress sites for over 1200 security flaws.
Wireshark
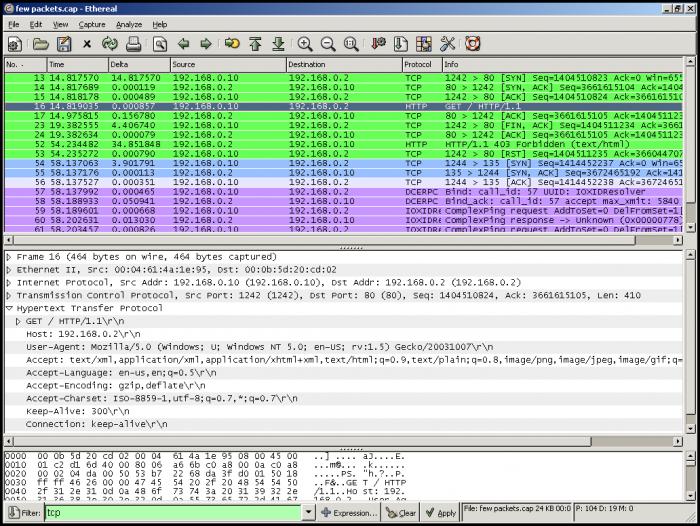
Ethereal was the previous name for this open-source program. TShark is an alternative to Wireshark’s CLI that provides a text-based interface. This GTK+-based network protocol analyzer works smoothly on Linux, Windows, and Mac OS X.
With Wireshark, you may capture and interactively browse the contents of network frames with the help of a GTK+-based network protocol analyzer or sniffer. The project aims to make a commercial-quality Unix network analyzer available and improve upon Wireshark by including features that aren’t present in proprietary network sniffers.
oclHashcat
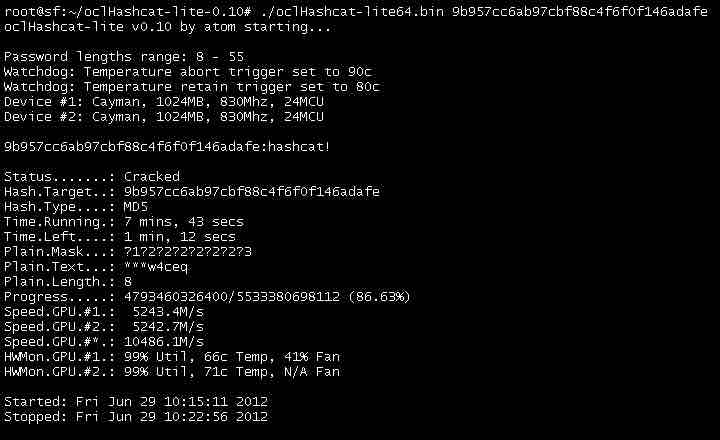
For free, you may obtain this useful hacking tool on Linux, OS X, and Windows. Hashcat is a free password-cracking program that you might be familiar with if you crack passwords frequently.
Whereas Hashcat relies on your central processing unit (CPU), oclHashcat uses your graphics processing unit (GPU). You can also use the program to crack WiFi passwords.
oclHashcat claims to be the first and only password-cracking tool because of its GPGPU-based engine. ForceWare 346.59 or later is required for NVIDIA users, whereas Catalyst 15.7 or later is required for AMD users.
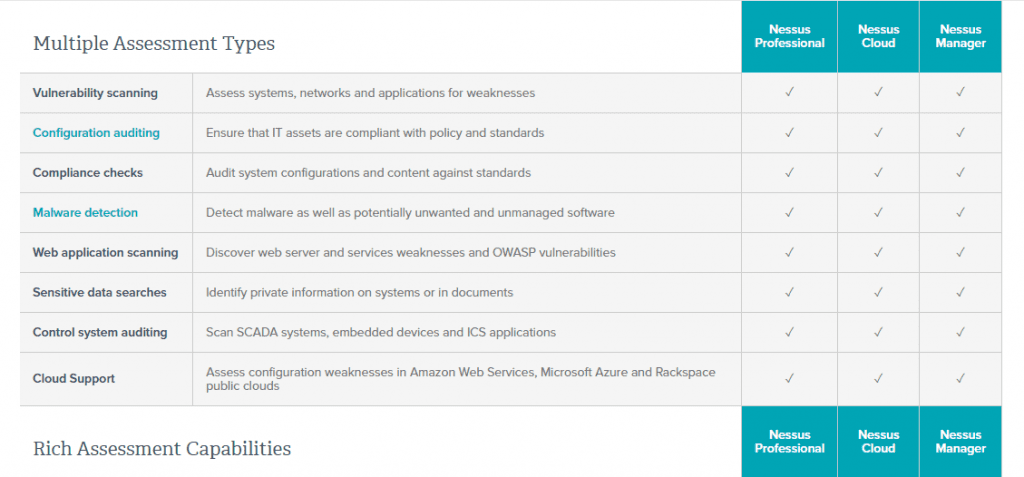
Nessus Vulnerability Scanner
Supported operating systems range from Windows 7 and 8 to Mac OS X and major Linux distributions like Debian, Ubuntu, Kali Linux, etc. The client-server model is at the heart of this finest free hacking tool of 2020.
Tenable Network Security developed what is now one of the most used vulnerability scanners. Each version of Nessus—Nessus Home, Nessus Professional, Nessus Manager, and Nessus Cloud—serves a different purpose.
Maltego
This program works equally well on Mac OS X, Microsoft Windows, and Linux. Maltego is a free and open-source forensics application that allows users to gather and mine massive amounts of data to create a picture of potential cyber threats in their environment.
You can demonstrate the complexity and severity of potential failure spots in your infrastructure and environment with the help of Maltego.
Social-Engineer Toolkit
However, Mac OS X and Windows, in addition to Linux, have limited support for the Social-Engineer Toolkit. On Mr. Robot, social engineering attacks like credential harvesting and phishing are simulated using TrustedSec’s Social-Engineer Toolkit, a complete framework for simulating these and other social engineering attacks.
Nessus Remote Security Scanner
It’s recently gone closed source, but you can still get it for free for the most part. More than 75,000 companies worldwide use Nessus as their primary vulnerability scanner for the Remote Security Scanner.
Many of the world’s leading corporations save a ton of money by employing Nessus to conduct audits of mission-critical corporate devices and apps.
Kismet
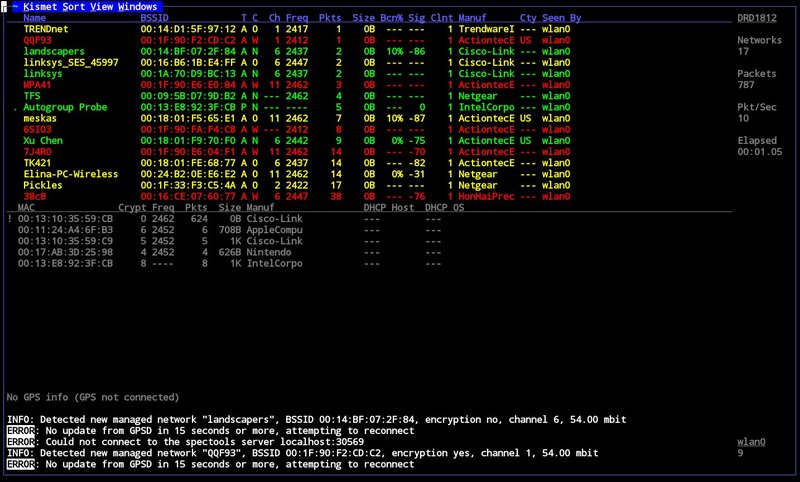
It is an 802.11 layer2 network sniffer, detector, and intrusion detection system. With the raw monitoring (mon) mode and the ability to sniff 802.11b, 802.11a, and 802.11g traffic, Kismet is compatible with any wireless card. If your wireless card has the capability, from is a handy function.
John The Ripper

It is open-source software, meaning the source code is freely available to anybody. Password-cracking software, to be precise.
Because it incorporates many password crackers into a single package, automatically identifies password hash types, and contains a configurable cracker, it is one of the most popular tools for testing and cracking passwords.
Unicornscan

Unicorns is a project that aims to build a Distributed User-Land TCP/IP stack for data analysis and aggregation. It’s meant to provide researchers with a high-quality interface for sending stimuli to and receiving responses from TCP/IP-enabled devices and networks.
This tool can do active/passive remote OS, application, and component identification by analyzing responses, and it supports asynchronous stateless TCP scanning with all TCP flag variants.
Netsparker

It’s a user-friendly web-based application vulnerability scanner that uses cutting-edge Proof-Based vulnerability scanning technology and incorporates penetration testing and reporting.
Netsparker safely and non-destructively exploits the identified flaws and generates exploitation evidence.
Burp Suite

Burp Suite is a comprehensive environment for assessing the safety of online applications. Equally impressive, it’s also one of the best hacking tools you can find online.
From the initial mapping and analysis of an application’s attack surface to detecting and exploiting security issues, the entire testing procedure is made possible by its many tools.
Superscan 4
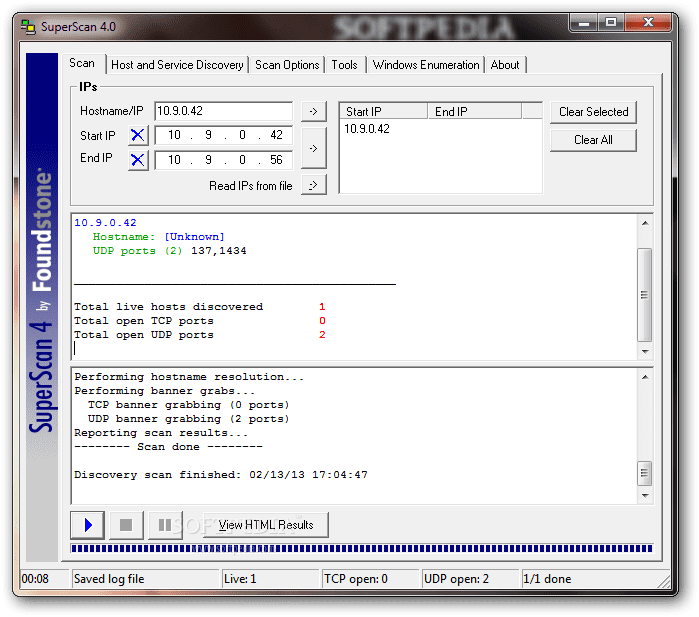
In any case, it’s another popular Windows port scanner. Fortunately, there is SuperScan, a robust TCP port scanner, pinger, and resolver. This zero-cost application scans a host for open TCP and UDP ports through a network connection.
Aircrack
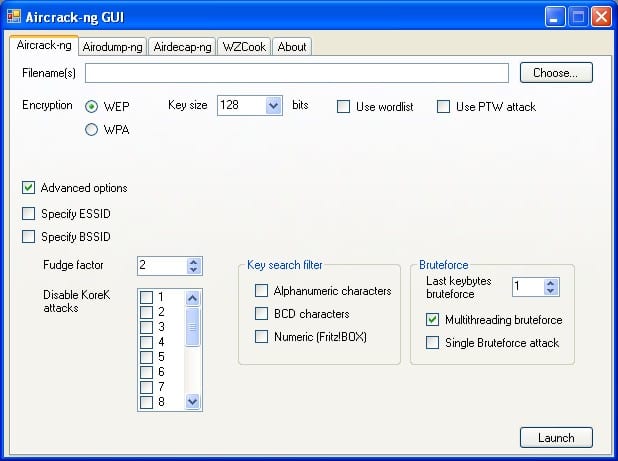
It includes a sniffer for detecting networks, a cracker for WEP and WPA/WPA2-PSK, and an analyzer for finding security flaws.
Several monitoring, attacking, pen testing, and cracking tools are available in AirCrack. Among the best network tools, this is in the top tier. This means it’s a top-tier WiFi hacking tool.
w3af
W3af is the best open-source and free web application security scanner available. A lot of people in the hacking and security research communities utilize that.
The web application attack and audit framework (w3aF) is utilized during penetration testing to collect data on security flaws.
OWASP Zed

The Zed Attack Proxy has risen to prominence as one of the most successful OWASP initiatives. When it comes to hacking and penetration testing, OWASP Zed is a reliable and simple tool.
Security researchers can locate vulnerabilities and defects with the help of OWASP Zed’s many resources.
Nikto Website Vulnerability Scanner
Penetration testers frequently use this tool. Nikto is a free, open-source tool for scanning web servers for security flaws.
Furthermore, more than 1300 servers are scanned for out-of-date software by the application. The Nikto Website Vulnerability Scanner also checks for issues with the server configuration.
SuperScan
One of the best free Windows port inspection tools, it uses the connect protocol to scan for open ports. Open TCP and UDP ports on the target computer can be found using the application.
SuperScan also supports basic searches like whois, traceroute, ping, and many more. Because of this, SuperScan is yet another leading hacking tool to think about using.
FAQs
Can these be used to break into internet accounts?
Programmers developed this kind of software specifically to spot security holes. No, we do not encourage account hacking because of the potential legal ramifications.
Is it risk-free to use these tools?
To avoid potential danger, only use the tools obtained from trusted sources.
Can I use these instruments to do a network scan?
A WiFi scanner is required for scanning a WiFi network. There are a few WiFi scanners mentioned in the post that may be able to provide some useful web data.
Therefore, the Best Windows, Linux, and mac hacking tools are those listed above. Write them down in the comments if you’re having problems. Do your friends a favor and forward this article to them if you find it helpful.



