Subscribe to Updates
Get the latest creative news from FooBar about art, design and business.
Author: Oliver
In the demon slayer, the 12 kizuki are the most infamous demons. Demon Lord Muzan Kibutsiji hand-picked these demons to carry out his evil desires and help him keep the demon hierarchy in order. In the English dub of the anime Demon Slayer, these demons are referred to as the twelve demon moons, the second-highest ranking members of the demon hierarchy, below only the demon king. If you’ve seen Demon Slayer, you know that if a human drinks the blood of the demon lord Muzan, it will permanently change them into a demon. The most powerful demons in Devil Slayer…
The Internet’s lack of restrictions is deceptive. As a result of government and ISP-imposed censorship, several websites are blocked from user access. ISPs and governments have implemented firewalls to prevent access to some websites. There are, however, workarounds that allow you to visit restricted sites. You can use a youtube proxy server, a virtual private network, or a domain name server (DNS) to gain access to a website that is blocked in your country. When it comes to websites that are blocked, YouTube is frequently mentioned. That website is one of the most often prohibited ones around the globe. Many…
Rockstar’s Grand Theft Auto 5 is one of their games that has remained popular eight years after its first release. Without a doubt, Grand Theft Auto 5’s story mode is fantastic. However, Grand Theft Auto Online (GTA Online) is what keeps the game going strong. This article will be about the fastest automobiles in Grand Theft Auto 5 and Grand Theft Auto Online, as you probably guessed. Grand Theft Auto Online players and Grand Theft Auto 5 love racing their supercars through the city at top speeds. Despite this, the vast selection available might be challenging to find the fastest…
Easy types of hack allow hackers to acquire sensitive information you may not want to share. Protecting yourself online may require familiarity with common hacking methods like phishing, distributed denial of service attacks, clickjacking, etc. Because of this, it’s important to know the common hacks used to steal sensitive information. Top 10 Common types of hack You Should Know About Bait and Switch – most dangerous types of hack Bait and switch is one of the types of hack in which the hacker pays for advertising space on a target website before launching the attack. It may take a user…
How to download from pirate bay? Torrent’s declining popularity nonetheless, it continues to be a vital part of the web. Using torrents to acquire freeware is perfectly legal if you download Linux distribution ISOs, free games, etc. However, you are inviting difficulty for yourself if you use it to download anything subject to intellectual property laws. It is legal for many users to obtain software using torrents because it is distributed anonymously. We’re talking about Torrent because many of you have written in recently wanting to know where to download it from the PirateBay. Many users have asked about this,…
Daily, the danger posed by Coronavirus increases. The entire country was on lockdown, and the authorities told everyone to stay inside. There’s nothing left to do here, and we’re bored out of our minds. Video chatting and online gaming are always options, but watching a movie with good company is more fun. Numerous websites now offer functions that allow watching movies in a group setting. You’ll find the best apps to watch movies with friends in this post. List of 8 Best apps to watch movies with friends This post will cover the best apps to watch movies with friends.…
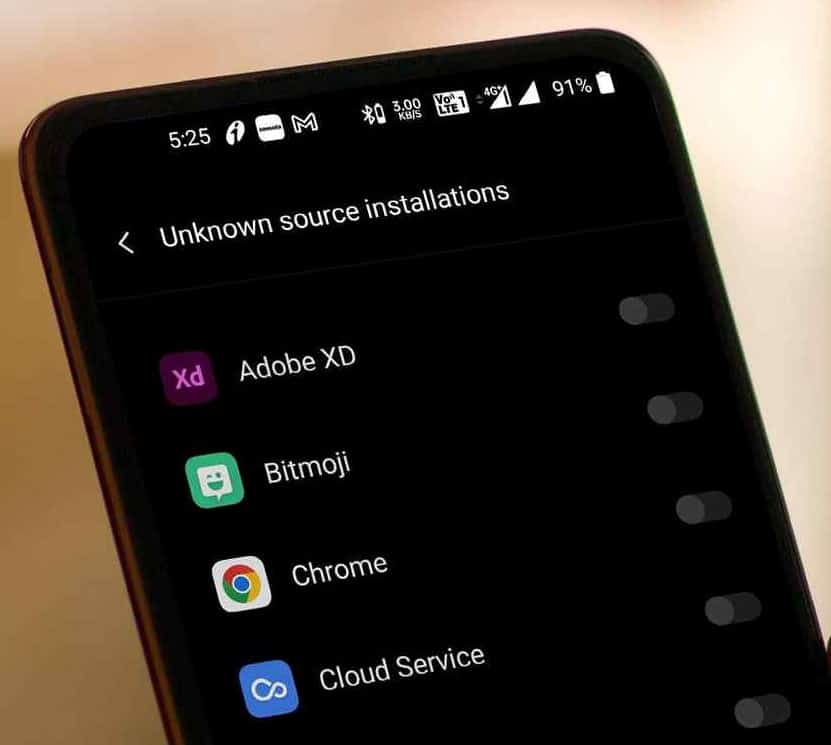
Unknown sources keeps turning on: Whatever the case may be, Android has evolved into a highly capable mobile OS. Since then, interest in it has increased dramatically. Its widespread adoption can be attributed to the extensive personalization options it provides to its users. The Android mobile operating system has its share of problems, just like every other OS. The latest reports suggest that a few Android users have encountered an unusual problem. Android users have noted that the ‘Unknown Source’ setting is always on. Users have also reported that deactivating “Unknown Sources” in the settings has no effect and that…
How to join the metaverse on oculus: You have most likely heard of Metaverse through your involvement with social networking sites. You have probably also heard several of your classmates talking about Metaverse. To begin with, let’s define Metaverse. How does one enter? We’ll do our best to respond to any questions you may have about the Metaverse. First, let’s agree on what it is. What is Metaverse? The term “Metaverse” refers to a mashup of “virtual reality,” “augmented reality,” and “real life.” This means that the line between your online and offline interactions becomes fuzzier. It’s a virtual world,…
Unethical hacking is the other side of the coin to the more popular ethical hacking. Hackers used illegal hacking techniques to rake in rapid cash. There are, however, many people who prefer to learn hacking the right way. Ethical hacking extends to areas such as WiFi protocol study and WiFi security. Therefore, you need to learn how to properly use specific instruments if you want to become an expert ethical hacker. With these resources, the security industry could eliminate a lot of unnecessary complexity. We’ve compiled a list of the Best Windows, Linux, and mac hacking tools, replete with in-depth…
The ability to code is the single thing that has made computer engineers smart enough to develop all the new things in the digital world, and this is the age of intelligence. For those interested in developing or programming for Android, we have gathered a list of the top android apps for developers. If you own an Android device, you may use these useful applications to learn how to code. Those who have a knack for coding can take advantage of some of the best android apps for developers currently out there. Coding is the only thing that makes computer…